No matter how many times I have to add and connect a Windows PowerShell host into vRealize Orchestrator I always seem to have issues. It’s not a difficult task but authentication issues between the Windows host and vRO are a very common sight. Compound that with a Windows host that is domain joined to Active Directory and it’s enough to drive you crazy. Below I discuss the steps I use to prep and add a Domain Joined Windows host into vRealize Orchestrator 8 running embedded on vRealize Automation 8.
Configuring the Windows Host
Before you add a Windows PowerShell host into vRO 8 there’s a few things that need to be configured. The first and most obvious is the Windows PowerShell host itself, which must be configured for remote access. In the below example I use a Domain Joined Windows 2016 Server. Next we need to enable this host for PowerShell remoting so that vRO can connect into it. A search online and you will find soooo many different ways to do this. I, however, have found that Ansible has a good guide on the steps to enable a Windows host with WinRM. Within this Ansible guide they have a link to an Ansible GitHub script that can configure a host for WinRM. This script has never let me down in setting up a host with the required settings for PowerShell remoting.
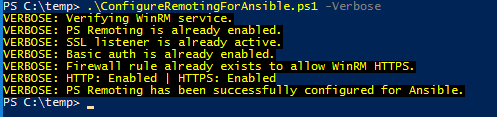
The script is very flexible and can be configured for your particular security requirements. You can download it from the Ansible GitHub page above and run it locally on the host you are configuring.
Configuring Kerberos
If you try to add a Windows Domain Joined host into vRO 8 at this point you will receive a few different Kerberos errors. A common error you might see is
Invalid name provided (Mechanism level: KrbException: Cannot locate default realm)
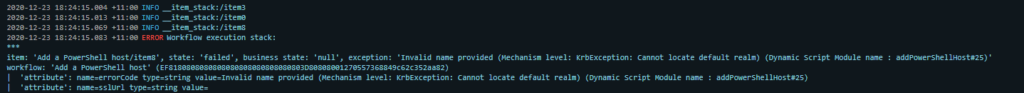
This relates to vRO8 not being setup for Kerberos authentication. To fix this we need to SSH onto the vRealize Automation 8 server and edit / create a krb5.conf file.
When using vRO embedded on vRA 8 the file is located at /data/vco/usr/lib/vco/app-server/conf/. There’s a good chance that this file doesn’t exist so you will need to create it.
cd /data/vco/usr/lib/vco/app-server/conf/
vi krb5.conf
Paste the below into the file and replace YOURDOMAIN with ‘your’ domain… eight times!
[libdefaults]
default_realm = YOURDOMAIN.COM
[realms]
YOURDOMAIN.COM = {
kdc = dc.yourdomain.com
default_domain = yourdomain.com
}
[domain_realm]
.yourdomain.com=YOURDOMAIN.COM
yourdomain.com=YOURDOMAIN.COM
Exit and save the file with :wq!
Change the permissions on the file
chmod 644 krb5.conf
We now need to redeploy the vRO Kubernetes pod so that it reads our new Kerberos configuration file.
We first need to find the vRO pod that’s running.
kubectl -n prelude get pods
This will give us a large list of pods running on our vRA host. We are looking for a particular vro pod with a large random ID number appended to it.
vco-app-<id>
Once we find this pod we need to use kubectl to destroy the pod. Kubernetes will then do what it does best and attempt to restart the Pod which will in turn use our new kerberos configuration.
kubectl -n prelude delete pod vco-app-<id>
We can use kubectl -n prelude get pods to monitor that a new pod is started. It will take a few minutes. Once started we can log out of the SSH session on the vRA 8 server.
Adding the Windows Host to vRO
With the Windows host configured for PowerShell remoting and vRealize Orchestrator 8 configured for Kerberos authentication we can now add the host into vRO using the inbuilt workflow.
Browse to the vRealize Automation UI. Click on Orchestrator on the Cloud Services Console. Navigate to Library / Workflows on the left pane. Then navigate to Workflows / Library / PowerShell / Configuration click on Add a PowerShell host and select run.
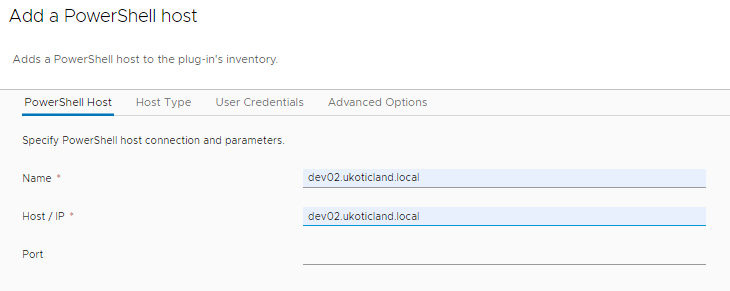
The workflow will request a number of parameters to be entered. The first section is the name and host to connect to. When connecting to a domain joined host you cannot use an IP address. You must use an fqdn if you want it to successfully connect.
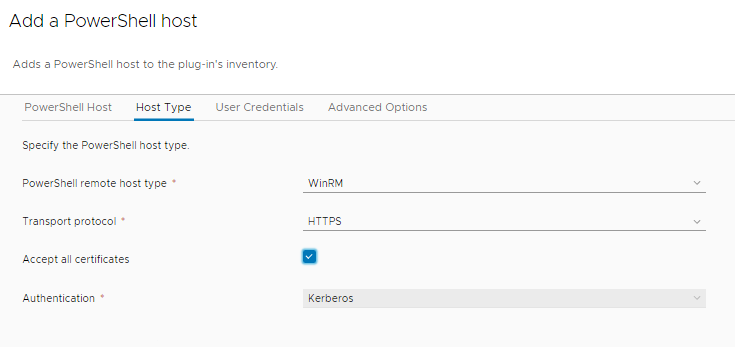
Next is the Host Type section. WinRM is the only option here. For the protocol it can be HTTP or HTTPS with a checkbox to accept all certificates. For Authentication change it from Basic to Kerberos.
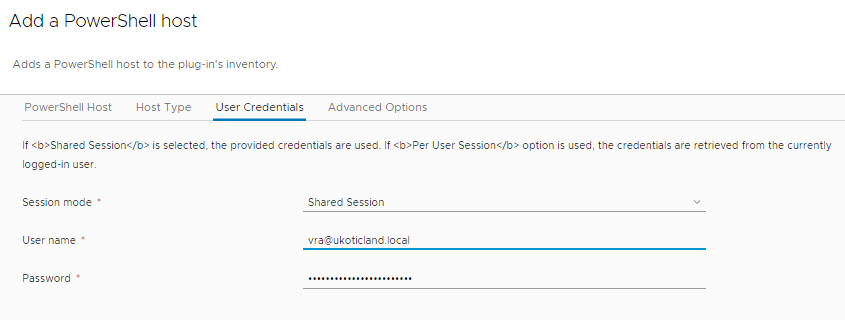
Next is User Credentials. For Session mode leave the default Shared Session. For User name you must use the format [email protected] when using Kerberos authentication.
You can skip Advanced Options and click Run. If all goes to plan you should see Completed and that the host was added successfully.
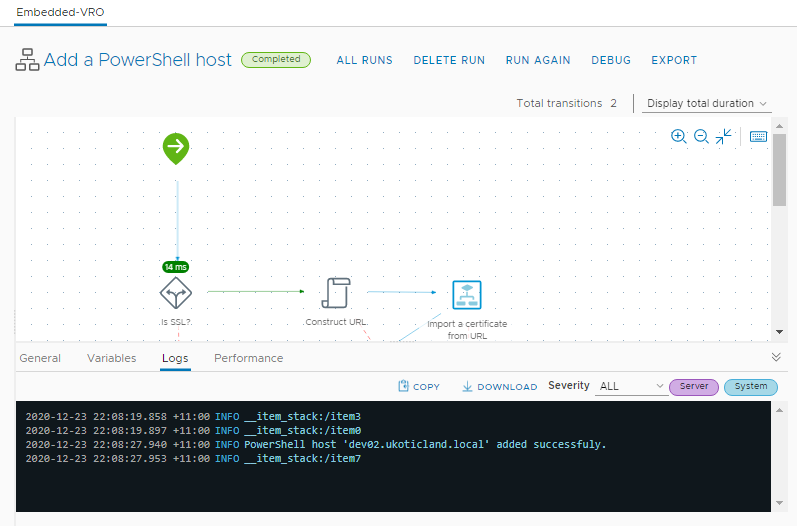
So as you can see there are a few steps that need to be performed to successfully add a Windows PowerShell host into vRealize Orchestrator. Even at the best of times this can be a tricky thing but hopefully the steps above will make it slightly easier.
References
VMware Docs -- Configure Kerberos Authentication
Ansible -- Setting up a Windows Host
Thank you for this! Saved me lots of trouble!
Would it be possible to add multiple powershell hosts? are there any drawbacks are issues with that
There are no issues adding multiple PowerShell hosts. It’s common when wanting to upgrade the OS version of the PowerShell host. In your vRO workflows you will write scripts that account for multiple hosts.