With the release of vRealize Automation 8.3 we now have feature parity with the SaaS based cloud version of vRA to manage and use Secrets in ABX. This is a long awaited features many of us have been patiently waiting for. Action secrets are basically stored encrypted values which you can leverage and use within your ABX scripts. They could be passwords, API Keys, or even something like a webhook URI.
Inside Cloud Assembly if you head over to Extensibility -> Actions. You will now see a new button called Manage Action Secrets. It’s here that you can create new secrets and manage current secrets.
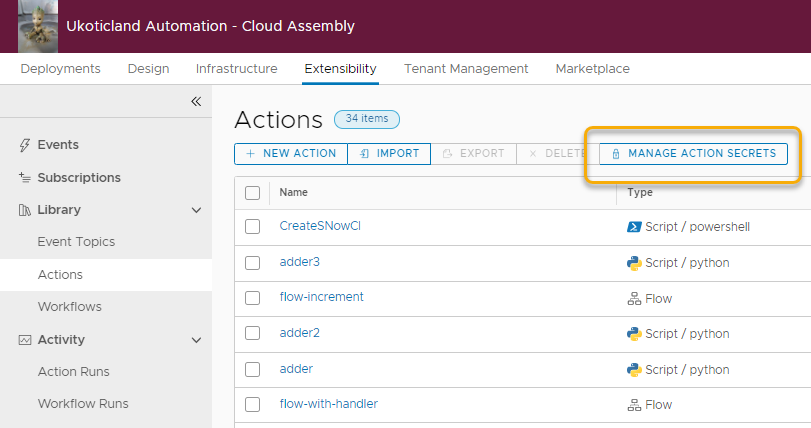
Note: As it stands today, Action Secrets are different to secrets held under the Infrastructure tab and used within Cloud Templates. They need to be managed separately.
Clicking on Managed Action Secrets takes you to the Action Secrets. It’s here that you can create new Action Secrets, Delete secrets, or edit an existing secret.
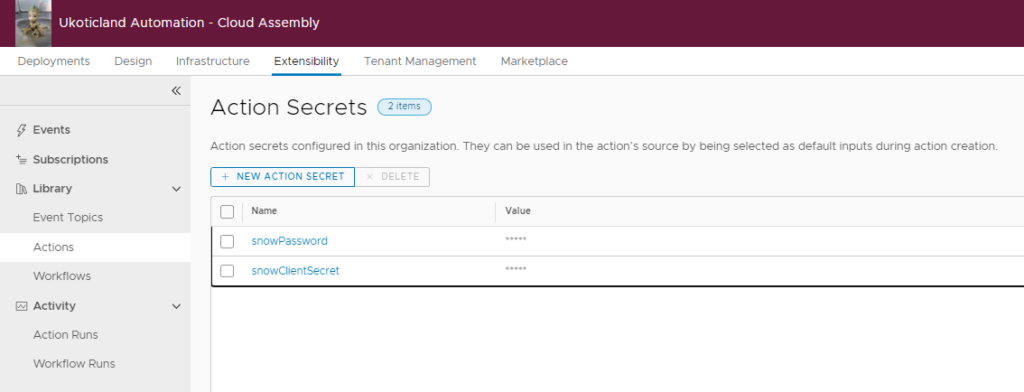
Creating Action Secrets
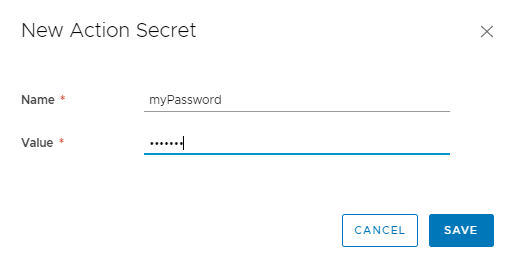
Creating an Action Secret is a straight forward process. In Cloud Assembly go to Extensibility -> Actions and click on New Action Secret. Define a Name, Value, and click Save.
Using Action Secrets
Using an Action Secret in a script is fairly simple. Let’s try it out using PowerShell. On Actions we click on New Action.
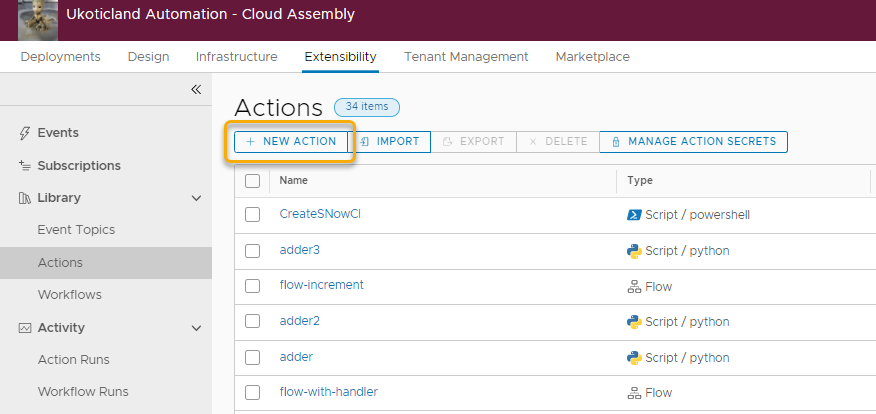
Let’s give the Action a Name, Description, and Project. For this example it really doesn’t matter, so we use getSecretValue as a Name and click Next.
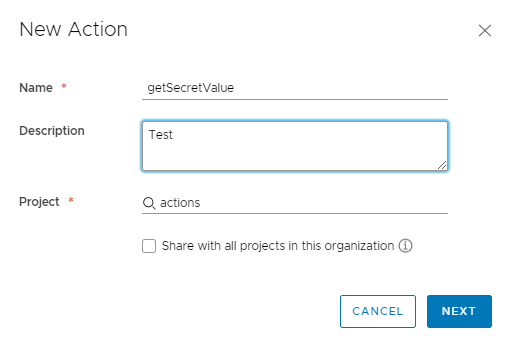
In the right pane we define our secret input we created above. To do this we check the box for Secret. This will allow us to select a secret from our pre-created Action Secrets.
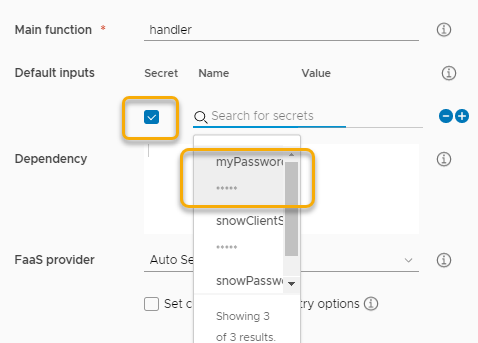
Note: Once you select a Secret from the list it becomes filter out from being able to be selected again.
In the left pane we select PowerShell as our language. Using the sample code that is provided we update the input variable to use our secret, $input.myPassword.
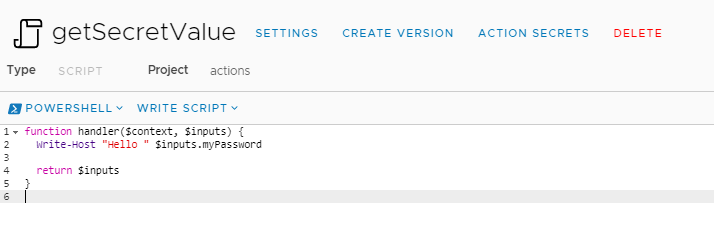
Running our Action without Decryption
We can try running our Action, as is, and see what our result looks like. What we see in our Inputs and Outputs as well as our running code, is an encrypted value of our defined secret. This is actually a good thing, in that our secret is passed from Cloud Assembly to our ABX script in encrypted form.
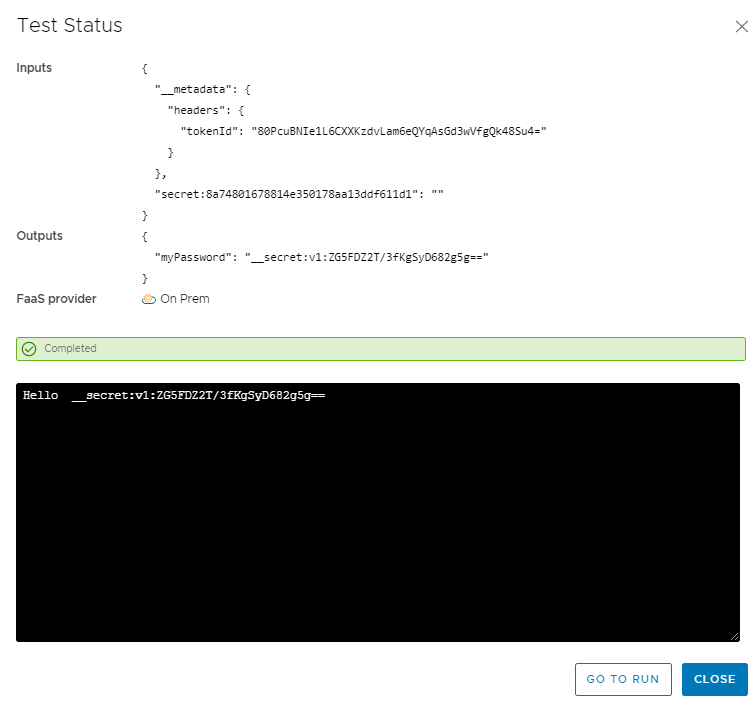
Running our Action with Decryption
To work with our Secret we need to decrypt it first. We do this by using an inbuilt function in our script.
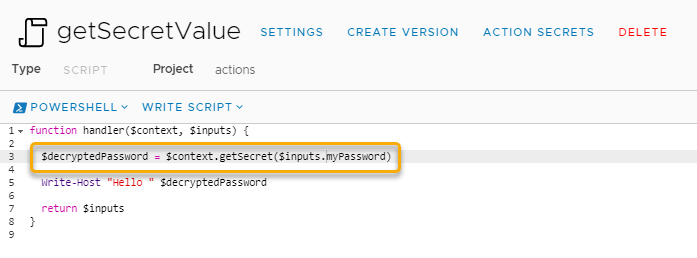
We call this function with $context.getSecret() and pass in our secret we want decrypted. In the example above I store the decrypted secret value to a variable called $decyptedPassword.
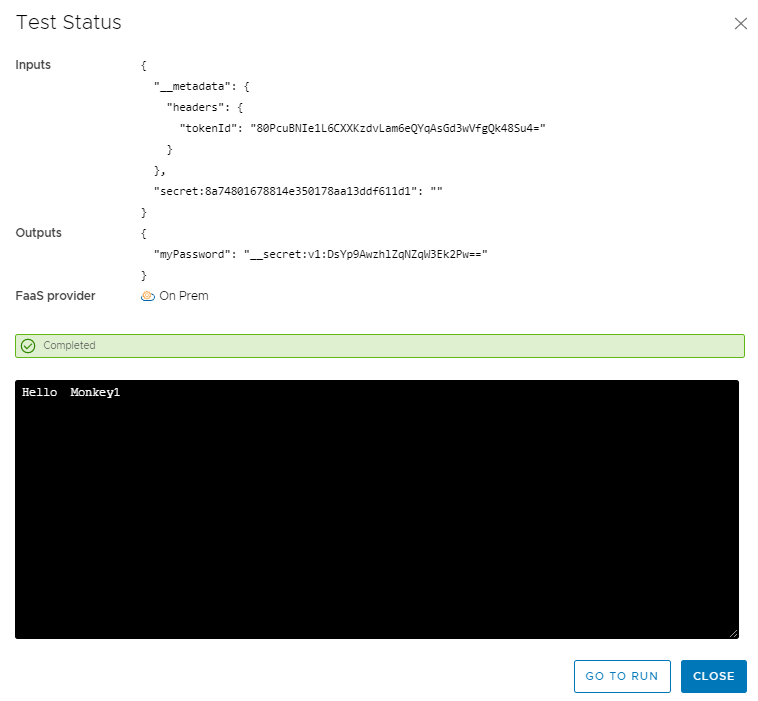
I can then reference that new variable and see the decrypted value. If I run another test this time while my Inputs and Outputs still show an encrypted value. My code output shows my decrypted value, Hello Monkey1 🙂
Using Python to Decrypt
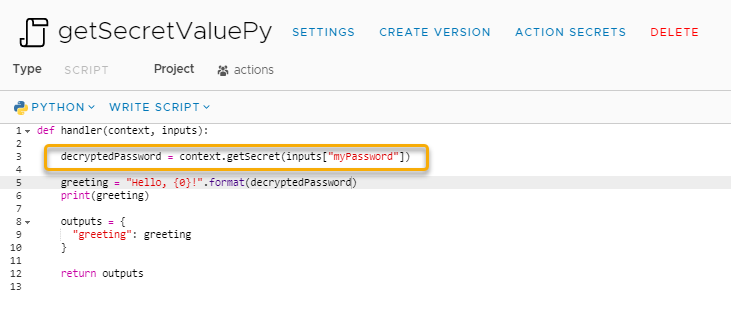
Now instead of PowerShell you may want to use Python. The great thing is that the process is almost identical to decrypt and use a secret value. Much like above with PowerShell, this time I switch the code to Python and slightly modify the sample code provided.
I run context.getSecret() and input my secret value in a format Python can understand. I then store that to the decryptedPassword variable, just like in PowerShell, and then print that to the screen.
This new added ability to work with Secrets, not just in the Cloud offering of vRA, but also the on-prem version is a welcome addition. Greatly increasing the value of using ABX and simplifying the use of working with passwords, API keys, tokens, etc.